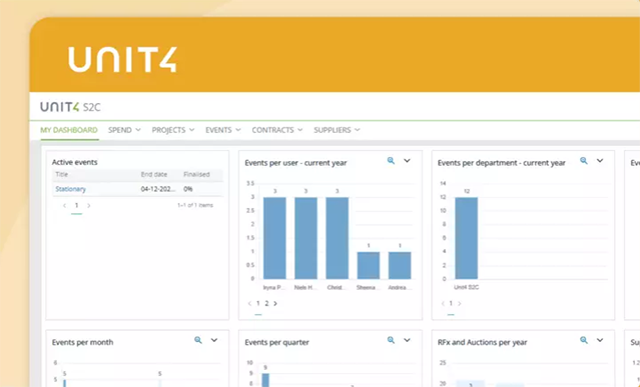
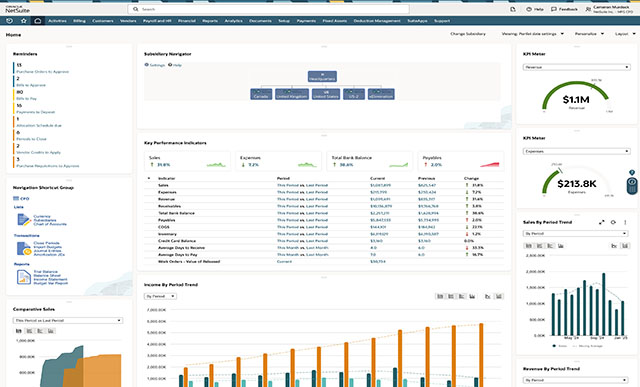
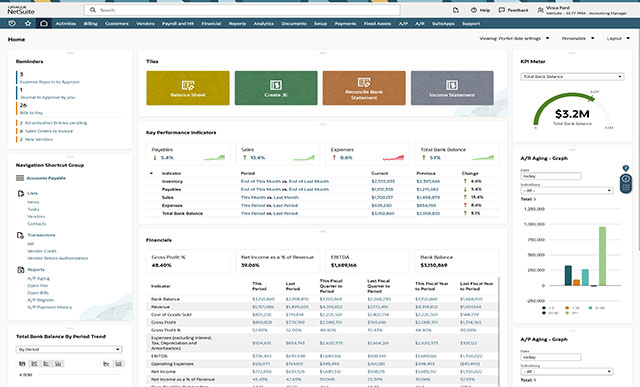
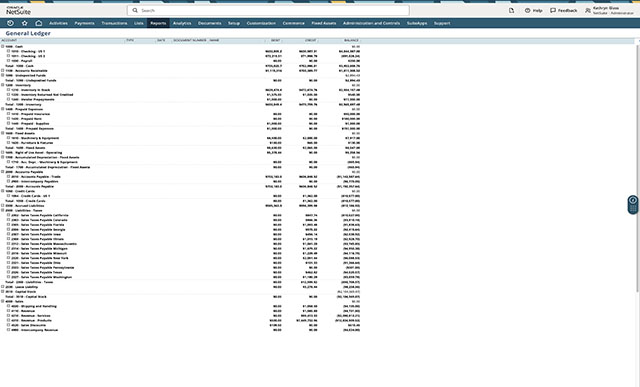
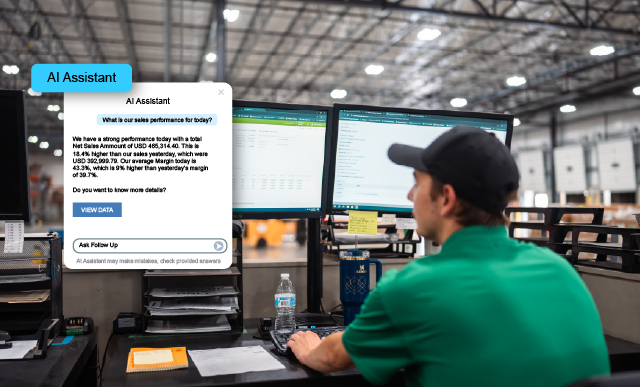
From evaluation of your need and selection of services, to adoption and optimization, our team is on hand to help you uncover the true value and possibilities of the Unit4 portfolio. We work hand in hand with your organization to get you up and running quickly, realize value and enhance and expand capabilities that drive continuous efficiencies for your business.
ERP Today has established itself as THE independent voice of the enterprise technology sector through its use of dynamic journalism, creativity and purpose.
Subscribe