The drive for digital sovereignty in the European Union (EU) is reshaping cybersecurity. Over the past decade, the digital sovereignty initiative has evolved from abstract, values-based statements to practical concerns regarding the speed and scope of implementation.
As regulations take full effect, business leaders are rethinking cybersecurity—how they secure data, manage third-party dependencies, and embed governance.
Cybersecurity is becoming a more visible and strategically important discipline that integrates legal, operational, and technical perspectives. This redefines how cybersecurity professionals work in the EU, influencing global best practices and establishing a new regulatory model that may inspire other countries in their own reforms.
A New Paradigm
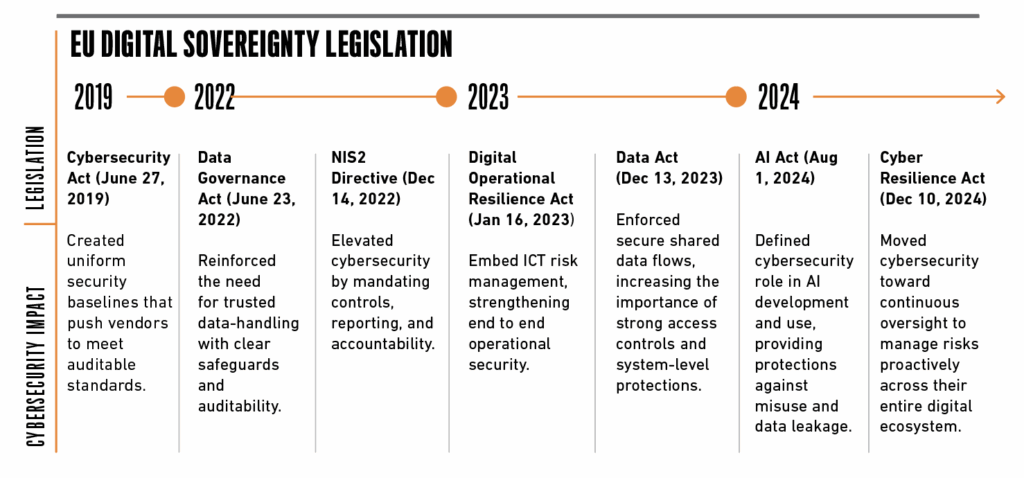
Historically, cybersecurity initiatives have largely been driven by the need to protect sensitive and proprietary data in high-value solutions like ERP systems. However, EU digital sovereignty regulations have increasingly transformed it into a mandatory discipline, with policymakers prioritizing control over data, systems, and digital services within the EU.
The Cybersecurity Act, for example, introduced auditable, EU-wide security standards, matched with certification schemes that demonstrate compliance. More recently, the Cyber Resilience Act (CRA) made cybersecurity a mandatory part of manufacturing and service delivery.
These regulations, among others, have reshaped cybersecurity in the EU and established mandates that define a new way of working for professionals, including:
- Lifecycle-embedded security integrating design, deployment, updates, and decommissioning into ongoing responsibilities
- Jurisdictional awareness ensuring daily tasks and strategic decisions align with EU legal frameworks and digital sovereignty regulations
- Infrastructure alignment directing attention toward the critical systems and networks being protected
- Proactive risk management identifying and mitigating threats and vulnerabilities before incidents occur
- Collaborative governance coordinating efforts across internal units, external vendors, and regulators to maintain accountable, auditable security practices.
These principles not only inform how professionals work, they drive demand for dedicated infrastructure, tools, and capabilities. This demand has, in turn, necessitated investment from cloud and enterprise providers that seek to establish digitally sovereign environments for professionals ready to embrace the new paradigm.
The Market Response
As EU regulations take hold, leading cloud and enterprise providers are investing in the infrastructure, capabilities, and partnerships required for digital sovereignty.
Currently, Oracle has announced plans to invest €2.58 billion ($3 billion) in EU cloud and AI infrastructure, while AWS has committed €7.8 billion ($9 billion) to expand its cloud footprint in Europe. SAP, meanwhile, has earmarked more than €20 billion ($23 billion) for an integrated sovereign-cloud platform that combines infrastructure, applications, and AI under EU governance
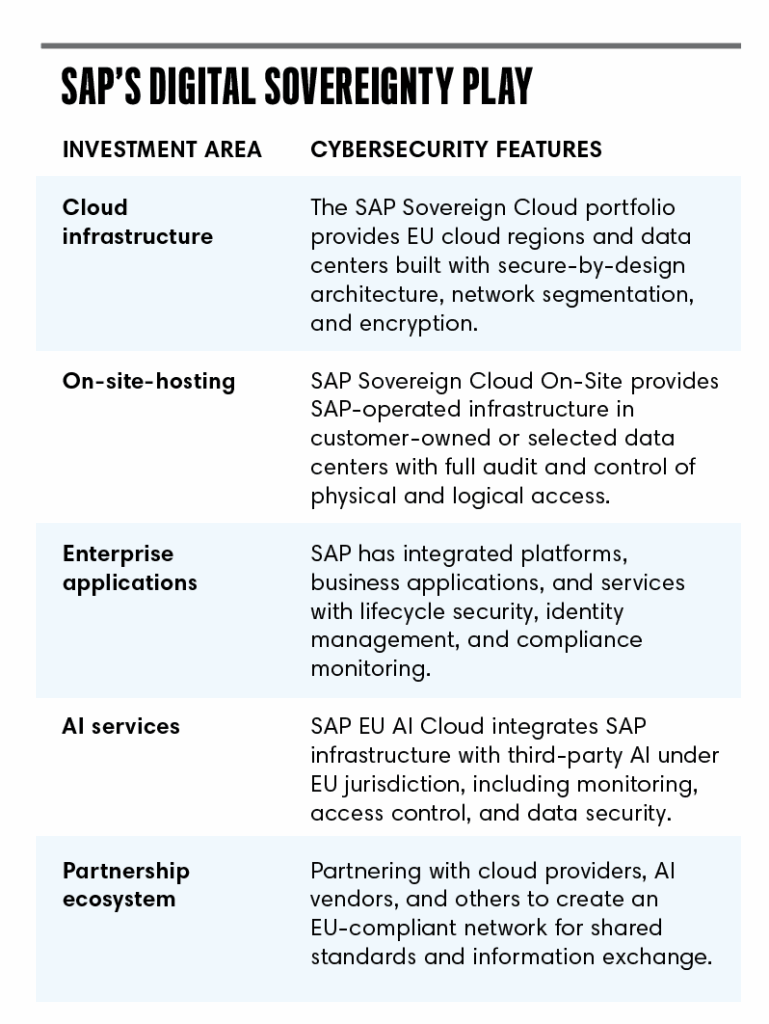
SAP’s larger investment reflects the breadth and depth of its stack: it must ensure every layer—from infrastructure and applications to data management, AI, and industry-specific solutions—meets requirements for EU sovereign.
As cloud providers establish sovereign infrastructure in the EU, best practices are trending toward clearly defined data boundaries and vertically integrated security controls. This puts cybersecurity at the forefront due to the critical role infrastructure now plays.
For example, SAP’s EU-based data centers and cloud regions create controlled environments where data, applications, and AI remain under EU jurisdiction. Cybersecurity teams can more readily embed protections across the full system lifecycle, turning infrastructure into a platform for continuous operational security.
New security-by-design frameworks, monitoring tools, and cross-border partnerships give teams real-time visibility and control, letting them manage risks more proactively. Meanwhile, strategic partnerships with regulators and vendors establish shared practices and workflows, enabling teams to coordinate governance across internal and external stakeholders, while contributing to collaborative governance structures.
 Impact Beyond Europe
Impact Beyond Europe
EU-sovereign infrastructure helps cybersecurity teams move from a reactive, compliance-focused posture to a more proactive, strategic, and self-sufficient security paradigm. Its impact will likely be felt beyond Europe in the years to come.
Foreign-headquartered companies that serve the EU market are already investing in local infrastructure, tools, and partnerships to comply with stricter regulatory standards. This creates a tipping point for broader adoption: EU-aligned practices may spread because they are effective, cost-efficient, or beneficial to customers.
Companies that already employ cybersecurity staff in the EU for regulatory compliance may find it more efficient to centralize security operations there. This would allow businesses to reduce cross-border data hurdles while extending EU-standard practices to less regulated markets abroad.
Alternatively, companies that ensure lifecycle-integrated security could find it not only meets EU audit requirements but differentiates products in other markets. This can simplify production in global sourcing hubs, lower supply chain risk, and build trust with new customers in emerging foreign markets.
The so-called “Brussels Effect” goes further.
When the General Data Protection Regulation (GDPR) took effect in 2018, it exposed businesses worldwide to the impact of extraterritorial legislation. Since then, several major markets have adopted laws echoing GDPR data-protection principles.
Now, EU regulations are formalizing an approach to cybersecurity that integrates legal, operational, and technical knowledge into workflows. Countries modernizing their digital governance laws are likely to adopt elements of this model, especially around data-flow documentation, risk assessments, and locally governed systems.
Meanwhile, integrated governance regimes are attractive to governments that view digital sovereignty as a strategic asset or digital economies as growth engines. Business leaders need to prepare for legislation that integrates security throughout a product’s lifecycle, enforces jurisdictional awareness, and aligns critical infrastructure with national interests.
Supply-chain transparency also appears set to expand beyond targeted, sector-specific interventions in select European markets. A more widely enforceable mandate would make supply-chain visibility and third-party oversight core elements of risk management for cybersecurity teams, whether others adopt new regulations based on the EU model or not.
As these regulations take shape, EU cybersecurity principles—lifecycle-integrated security, jurisdictional awareness, and infrastructural alignment—are likely to become international benchmarks.
What This Means for ERP Insiders
Cybersecurity has become more visible. EU digital sovereignty transforms cybersecurity into an operational discipline that ERP teams must integrate across design, deployment, and governance. Enterprises are moving towards a unified framework for secure, consistent system operations as a result. This shift creates clearer expectations for how data flows are documented, how systems are maintained, and how risk is managed across interconnected ERP environments.
Infrastructure has become a strategic differentiator The market is reorganizing around platforms that treat security as a built-in advantage. Cloud providers are building sovereign environments that give ERP leaders predictable data boundaries and vertically integrated security controls. These investments accelerate the move toward lifecycle-embedded security, allowing ERP teams to design systems that meet regulatory requirements while reducing cross-border complexity.
EU standards are becoming international benchmarks. Enterprise technology is beginning to standardize around EU-driven security and data-governance norms. ERP programs operating across regions will increasingly follow EU-aligned governance, documentation, and infrastructure models. This creates a path toward unified security practices that reduce fragmentation, streamline global operations, and strengthen trust with regulators and customers.






